

Read the 2026 State of Identity Security Report
[GET REPORT]
The Permiso Platform discovers, protects, and defends human, non-human and AI identities in cloud and on-prem environments. Comprehensive visibility, prioritized risk reduction, and proactive threat defense for all identities.

.png)
CISO Guide to Detecting and Preventing Identity Attacks
Learn More
The Human Touch In Creating and Securing Non-Human Identities
Learn More
Subscribe to Cloud Chronicles for the latest in cloud security!

The Permiso Platform discovers, protects, and defends human, non-human and AI identities in cloud and on-prem environments. Comprehensive visibility, prioritized risk reduction, and proactive threat defense for all identities.

.png)
CISO Guide to Detecting and Preventing Identity Attacks
Learn More
The Human Touch In Creating and Securing Non-Human Identities
Learn More
Subscribe to Cloud Chronicles for the latest in cloud security!
© Permiso Security 2025
|Privacy Policy|TermsThe Permiso Identity Security Platform helps organizations secure their modern identity attack surface across all environments. The heart of our platform is the Universal Identity Graph.
We leverage the Universal Identity Graph to help customers discover and classify identities, protect them against vulnerabilities and exposures, and defend them against attacks with industry leading threat detection capabilities.
 featured content
featured content



You can't protect what you don't know. Permiso Discover gives enterprises a comprehensive identity inventory of all of your human, non-human and AI - wherever they live. Permiso Discover helps you quickly assess risk and harden your attack surface.
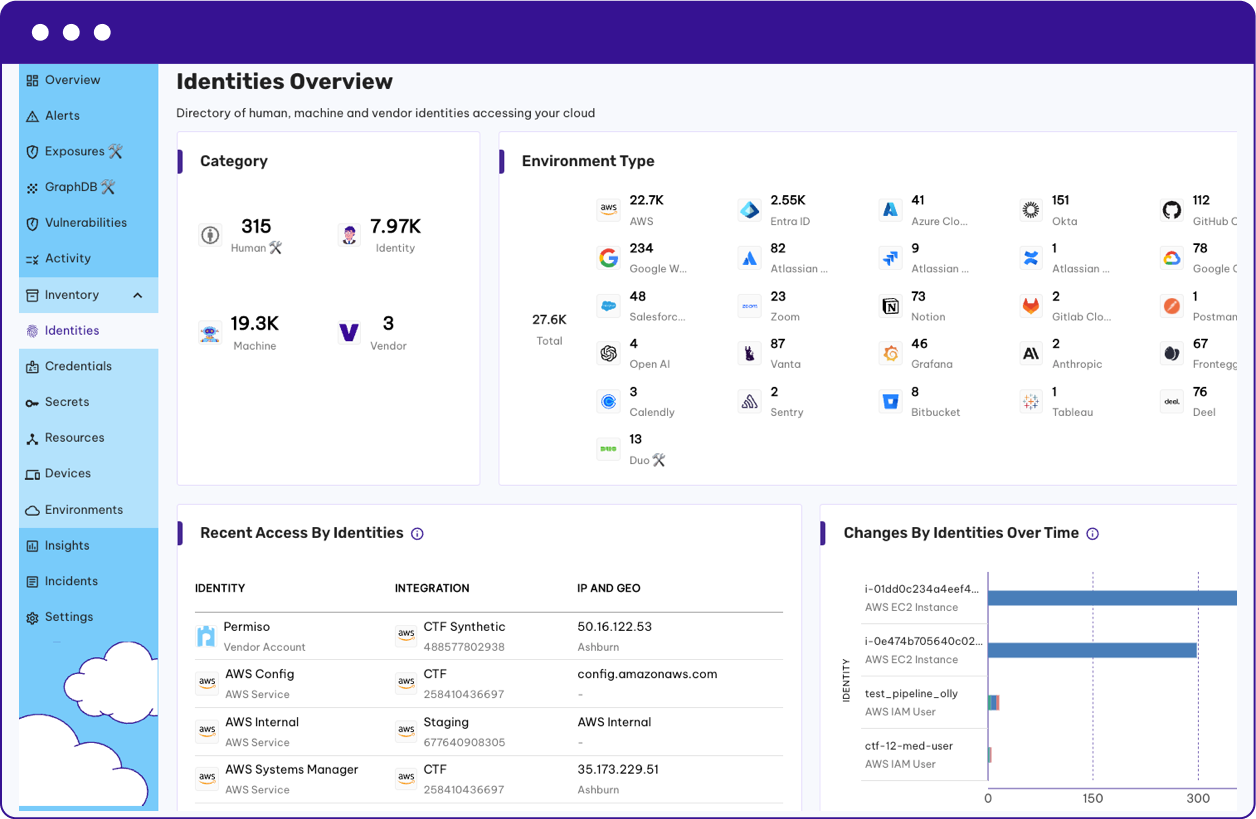

Instead of looking out there for high-priced “experts”, Permiso gives your security team the tools to be the experts you need now.

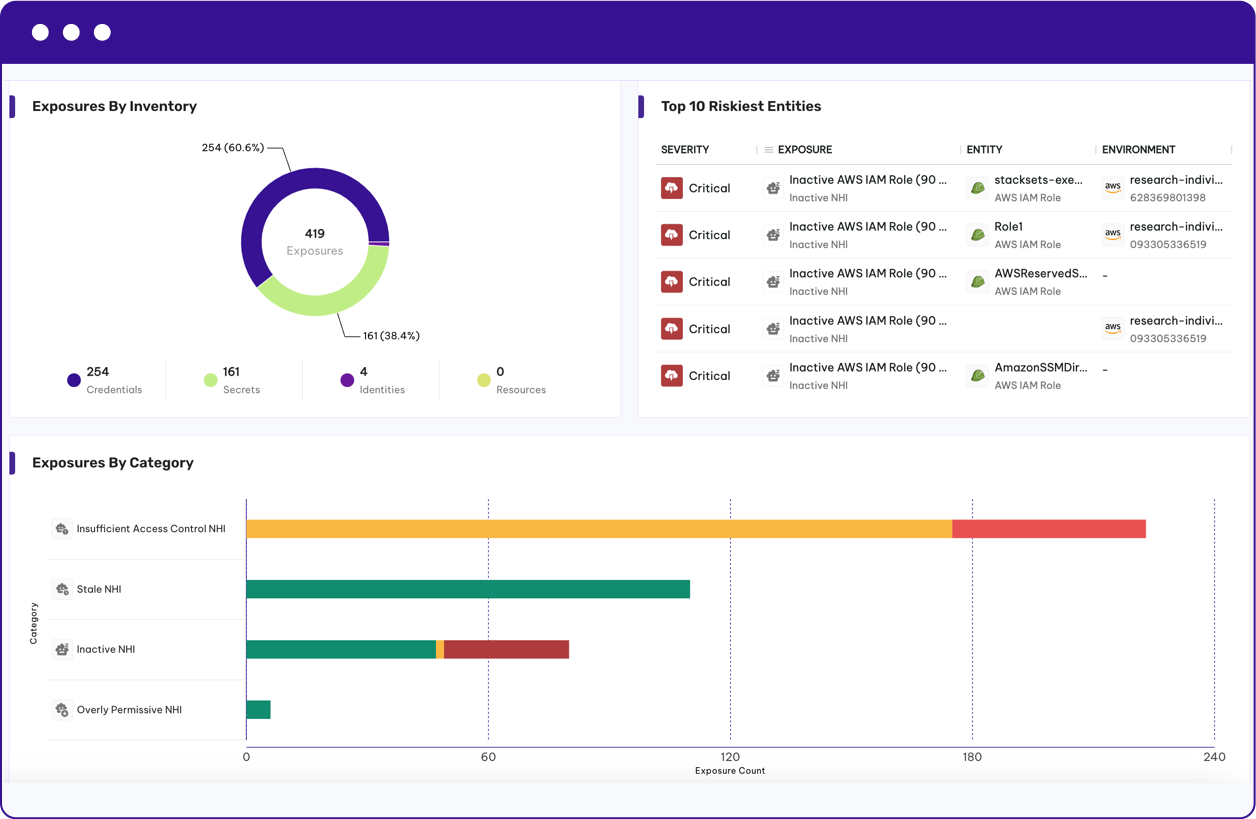
Permiso Protect continuously evaluates the risk posture of identities based on usage patterns, exposure, and entitlements. Surface and quantify high-risk identities, stale access, and toxic combinations across human, vendor, AI, and non-human accounts to identify those identities are most likely to be compromised.
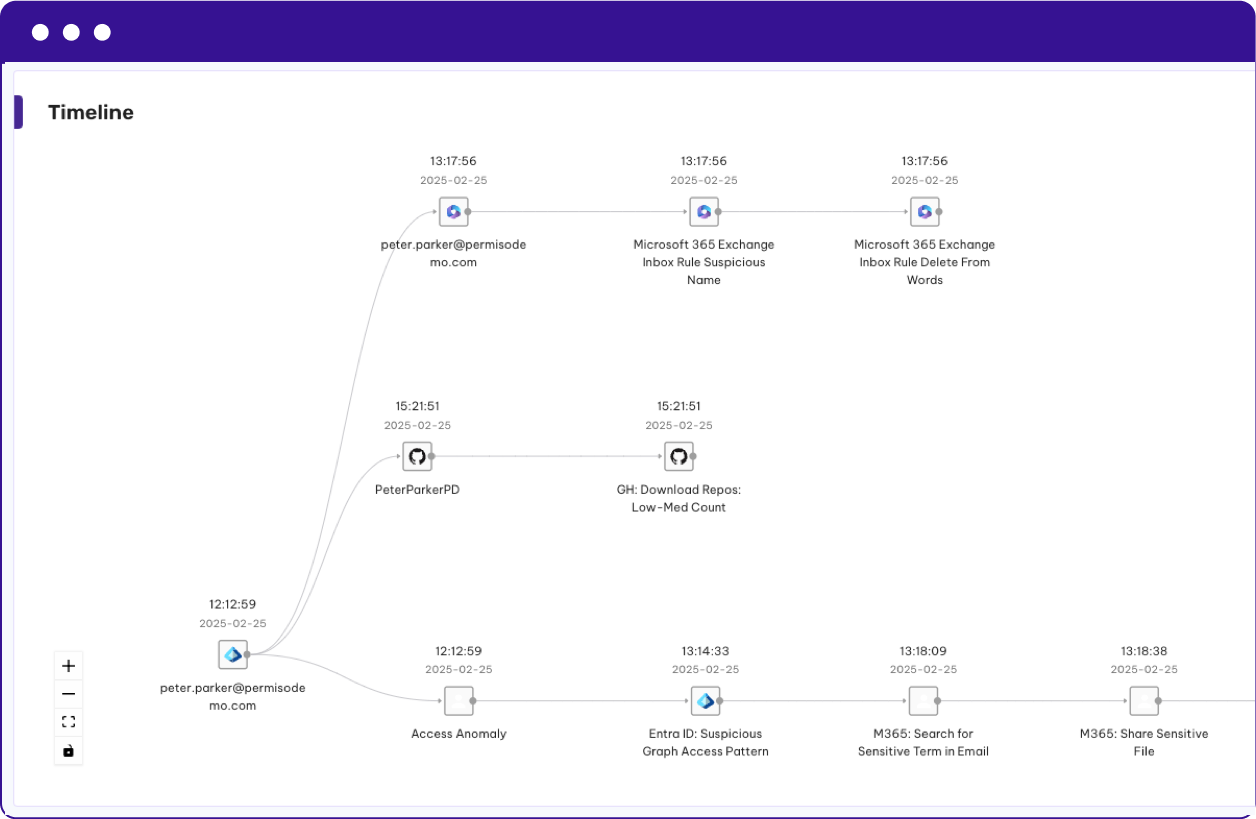
Continuously monitor for anomalous behavior, lateral movement, and early signs of compromise. Investigate identity-driven attacks with insight from runtime and control plane activity. Prioritize threats using high-fidelity, real-time risk signals.
Permiso Security’s secret sauce of runtime and static identity enrichment in the Universal Identity Graph enables tracking of identities across authentication boundaries, providing unparalleled visibility into all risk and threats, for human and non-human identities. A one stop shop for securing all of your identities across all environments.
Attain a comprehensive understanding of your true identify attack surface by stitching human, non-human, and AI-based identities together. Gain transparency into risk.
Permiso's Universal Identity Graph inventories all of your identities in all cloud environments, assesses exposure risk and identifies those identities are most likely to be compromised.
Comprehensive identity threat detection and response for all human and non-human identities to detect account takeover, credential compromise and insider threat.
Inventory all non-human identities, identify inactive, overly permissive, stale and orphaned NHIs, and monitor them for suspicious and malicious activity
Complete visibility, prioritized risk reduction, and proactive threat defense for all of your AI identities. See who’s using AI, who’s building with it, and which agents are active and what they are doing.


P0 Labs is our super brain R&D group that sniff out new ways to identify and eliminate the threats to cloud infrastructure that are evolving every day. Consisting of several ex-Mandiant advanced practices leads, the team has developed more than 1,500+ detection signals.
All the goodness of P0 labs' hunting campaigns delivered directly in to Permiso so your SOC can respond to cloud attacks and your organization can remain secure.
Oh, and by the way, we're constantly custom tuning rules and scouring your environment so don't be surprised when we request to give you a threat briefing.
.png)

Permiso’s ability to track identities and their activities across IaaS, SaaS, and identity providers at runtime is unlike any of our existing solutions.

Identity is the silver bullet in the cloud. If you don’t get it right, you’re dead!


Permiso unlocks unique visibility into my cloud infrastructure environment that I currently don’t get from a CSPM or SIEM.


Permiso has proven to be indispensable to the way we manage and secure identities across multiple cloud environments.


Request a demo, get more deets, or just say hi.
Subscribe to Cloud Chronicles for the latest in cloud security!